Protect your private emails with the latest cybersecurity solutions at Total Business Systems in Jacksonville, FL
Safer Emails
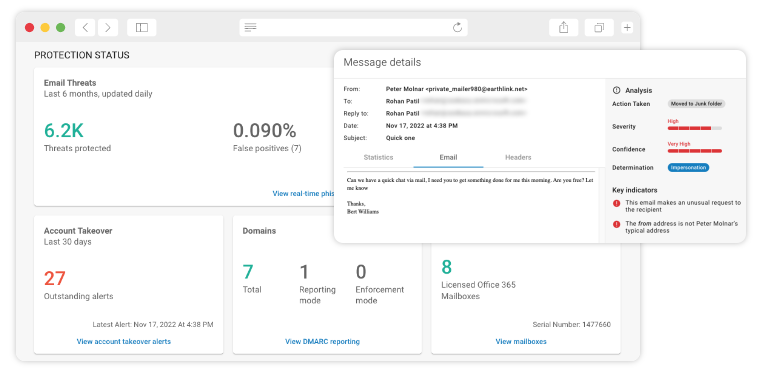
Industry leading email security for your business
AI-driven phishing attacks have surged by 1,265%
since the introduction of generative AI tools.
Experience unparalleled email security with the simplest, most thorough protection available.
Email Security, Archiving & Encryption
Professional Filtering Services
- Cloud-based protection
- Spam, malware, viruses & phishing
- Protect against zero-hour attacks
- Protection against ransomware
- Agentless email encryption
- Legal hold - 10 Years
- 256-bit encryption at rest and in transit
- LDAP and multi-factor authentication
- Up to 96 hours of email continuity
- Public key cryptography (RSA 1024)
Email Security, Archiving, Encryption & Impersonation Protection
Gain Advanced Artificial Intelligence
- Everything in Standard, Plus
- AI for real-time protection
- Stops spear-phishing attacks
- Business email compromise (BEC)
- Extortion & other social attacks
- AI to detect and stop email attacks
- Detects and alerts account takeover
- Blocks attackers’ account access
- DMARC authentication
- Prevent domain spoofing
Enterprise Email Security, Archiving, Encryption, Impersonation Protection & Microsoft 365 Backups
Add Compliance & M365 Backups
- Everything in Advanced, Plus
- Outlook Add-in & threat reporting
- Threat hunting
- Identify high-risk users
- Block future regional emails
- Impersonation and BEC insights
- Review users with malicious emails
- Automatically alert all impacted users
- Microsoft 365 backups
- Defend against cyber-threats
Top Cybersecurity Statistics
Threats, Tends and Challenges
- 85% of security pros say generative AI is accelerating new attacks (Ponemon, 2024).
- 70% say AI tools have caught threats humans would miss (Ponemon, 2024).
- 45% of organizations will be hit by a supply chain breach by the end of 2025 (Gartner).
- 97% of organizations reported more attacks since the Russia Ukraine war began (Accenture, 2024).
- 70% of breaches caused “significant or very significant” operational disruption (IBM).
- Phishing causes >90% of breaches (Hornetsecurity).
- Attacks up 4,151% since ChatGPT was launched (SlashNext).
- By 2027, 17% of cyberattacks will use generative AI (Gartner).
- Top impersonated brands: DHL, FedEx, Facebook, Mastercard, Netflix.
- Social media: 30.5% of phishing attacks now target these platforms.
- 47% of SMBs (under $10M revenue) were targeted last year.
- 25% of BEC attacks in Q1 2024 bypassed MFA, often using reverse proxy credential theft.

Actionable Tips:
- Run monthly cyber awareness training phishing simulations.
- Require MFA for all email accounts and privileged systems.
- Review and understand cyber insurance coverage and exclusions.
- Update board leadership quarterly on threat landscape and compliance status.
95% of cybersecurity breaches are attributed to human error
Security Assessment
Cyber Awareness Training
Provide unparalleled insight into your organization's first layer of defense, your employees.
All it takes is one employee to cause a data breach
Cybercriminals are diligent in finding new, sophisticated methods to trick unsuspecting individuals into putting themselves at risk.
Cyber Awareness Training
- Weekly Micro Training
- Employee Vulnerability Assessment (EVA)
- Simulated Phishing
- Outlook Phishing Plugin
- Dark Web Monitoring
HIPPA Cyber Awareness Training
- Weekly Micro Training
- Employee Vulnerability Assessment (EVA)
- Simulated Phishing
- Outlook Phishing Plugin
- Dark Web Monitoring
- HIPPA Privacy & Security Training
- HIPPA Annual Risk Assessment
- 18 HIPPA Policy & Procedures
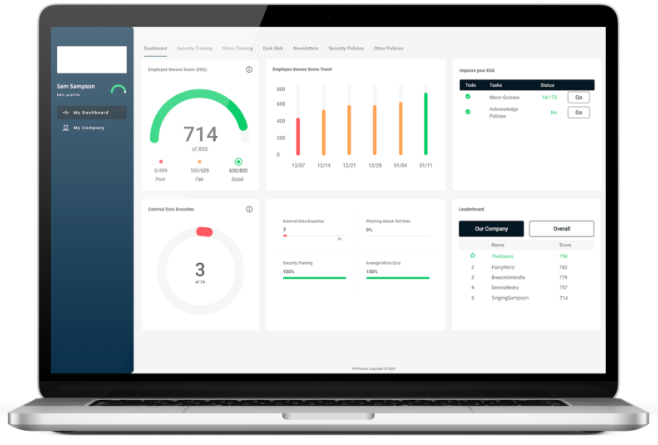
Continuous Education
Weekly 2-minute micro-training video & short quizzes to educate your employees.
TBS proactively monitors the dark web for compromised account data. The sooner clients are notified of a breach, the sooner they can change their passwords. End-users also have the ability to scan the dark web for their personal, friends, and family accounts with no limit.
Routine simulated phishing has been proven to minimize the risk of end-users falling victim to a malicious phishing attempt. Routine phishing instills into your employees the very behaviors of IT professionals before they click on any link so that even on the most chaotic of days, they're ready.
EVA identifies the human vulnerabilities and their related risks. Based on NIST standards, the Security Risk Assessment (SRA) assesses your administrative, physical, and technical vulnerabilities; identifies the associated risks, and provides recommendations for improvement.
For end-users, an interactive leaderboard ignites friendly competition with just their screen name's honor at stake. For managers, employee names are featured, with a report for performance evaluations, they can track just who needs more time bulking up!